Kubernetes Role-Based Access Control(RBAC)
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Role-Based Access Control (RBAC)
Kubernetes ina moduli yaidhinisha inayoitwa Role-Based Access Control (RBAC) ambayo husaidia kuweka ruhusa za matumizi kwa seva ya API.
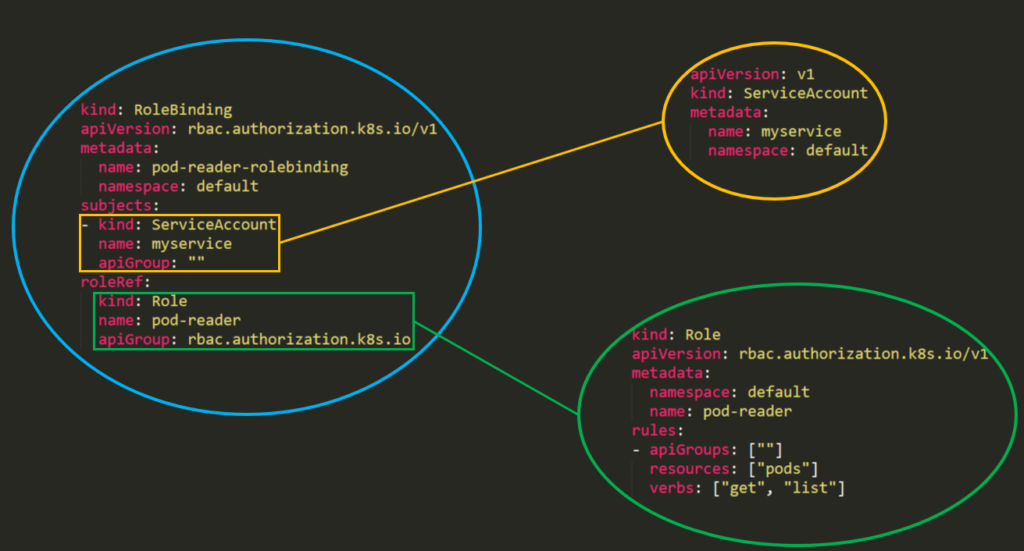
Mfumo wa ruhusa wa RBAC umejengwa kutoka sehemu tatu tofauti:
- Role\ClusterRole – Ruhusa halisi. Inajumuisha kanuni zinazowakilisha seti ya ruhusa. Kila kanuni ina rasilimali na vitendo. Kitenzi ni kitendo ambacho kitawekwa kwenye rasilimali.
- Subject (Mtumiaji, Kundi au Akaunti ya Huduma) – Kitu ambacho kitapokea ruhusa.
- RoleBinding\ClusterRoleBinding – Muunganisho kati ya Role\ClusterRole na subject.
Tofauti kati ya “Roles” na “ClusterRoles” ni mahali ambapo jukumu litatumika – “Role” itatoa ufikiaji kwa moja maalum namespace, wakati “ClusterRole” inaweza kutumika katika namespaces zote katika klasta. Zaidi ya hayo, ClusterRoles zinaweza pia kutoa ufikiaji kwa:
- rasilimali za kiwango cha klasta (kama vile nodi).
- mipangilio isiyo ya rasilimali (kama /healthz).
- rasilimali zenye majina (kama Pods), katika namespaces zote.
Kuanzia Kubernetes 1.6 kuendelea, sera za RBAC zime wezeshwa kwa default. Lakini ili kuwezesha RBAC unaweza kutumia kitu kama:
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
Templates
Katika template ya Role au ClusterRole utahitaji kuashiria jina la jukumu, namespace (katika roles) na kisha apiGroups, resources na verbs za jukumu:
- apiGroups ni array inayoshikilia API namespaces tofauti ambazo sheria hii inatumika. Kwa mfano, ufafanuzi wa Pod unatumia apiVersion: v1. Inaweza kuwa na thamani kama rbac.authorization.k8s.io au [*].
- resources ni array inayofafanua ni rasilimali zipi sheria hii inatumika. Unaweza kupata rasilimali zote kwa:
kubectl api-resources --namespaced=true - verbs ni array inayoshikilia vitendo vilivyokubaliwa. Kitenzi katika Kubernetes kinafafanua aina ya hatua unahitaji kutekeleza kwa rasilimali. Kwa mfano, kitenzi la orodha linatumika dhidi ya makusanyo wakati “get” inatumika dhidi ya rasilimali moja.
Rules Verbs
(Taarifa hii ilichukuliwa kutoka the docs)
| HTTP verb | request verb |
|---|---|
| POST | create |
| GET, HEAD | get (kwa rasilimali binafsi), list (kwa makusanyo, ikiwa ni pamoja na maudhui kamili ya kitu), watch (kwa kutazama rasilimali binafsi au mkusanyiko wa rasilimali) |
| PUT | update |
| PATCH | patch |
| DELETE | delete (kwa rasilimali binafsi), deletecollection (kwa makusanyo) |
Kubernetes wakati mwingine huangalia idhini kwa ruhusa za ziada kwa kutumia vitendo maalum. Kwa mfano:
- PodSecurityPolicy
- kitenzi
usekwenye rasilimalipodsecuritypolicieskatika kundi la APIpolicy. - RBAC
- vitendo
bindnaescalatekwenye rasilimalirolesnaclusterroleskatika kundi la APIrbac.authorization.k8s.io. - Authentication
- kitenzi
impersonatekwenyeusers,groups, naserviceaccountskatika kundi la API msingi, nauserextraskatika kundi la APIauthentication.k8s.io.
Warning
Unaweza kupata vitendo vyote ambavyo kila rasilimali inasaidia ukitekeleza
kubectl api-resources --sort-by name -o wide
Examples
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: defaultGreen
name: pod-and-pod-logs-reader
rules:
- apiGroups: [""]
resources: ["pods", "pods/log"]
verbs: ["get", "list", "watch"]
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
# "namespace" omitted since ClusterRoles are not namespaced
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "watch", "list"]
Kwa mfano, unaweza kutumia ClusterRole kumruhusu mtumiaji maalum kuendesha:
kubectl get pods --all-namespaces
RoleBinding na ClusterRoleBinding
Kutoka kwenye hati: Role binding inatoa ruhusa zilizofafanuliwa katika jukumu kwa mtumiaji au kundi la watumiaji. Inashikilia orodha ya mada (watumiaji, vikundi, au akaunti za huduma), na rejeleo kwa jukumu linalotolewa. RoleBinding inatoa ruhusa ndani ya namespace maalum wakati ClusterRoleBinding inatoa ufikiaji huo kote kwenye klasta.
piVersion: rbac.authorization.k8s.io/v1
# This role binding allows "jane" to read pods in the "default" namespace.
# You need to already have a Role named "pod-reader" in that namespace.
kind: RoleBinding
metadata:
name: read-pods
namespace: default
subjects:
# You can specify more than one "subject"
- kind: User
name: jane # "name" is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
# "roleRef" specifies the binding to a Role / ClusterRole
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io
apiVersion: rbac.authorization.k8s.io/v1
# This cluster role binding allows anyone in the "manager" group to read secrets in any namespace.
kind: ClusterRoleBinding
metadata:
name: read-secrets-global
subjects:
- kind: Group
name: manager # Name is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: secret-reader
apiGroup: rbac.authorization.k8s.io
Ruhusa ni za kuongezeka hivyo ikiwa una clusterRole yenye “orodhesha” na “futa” siri unaweza kuiongeza na Role yenye “pata”. Hivyo kuwa makini na kila wakati jaribu majukumu yako na ruhusa na eleza kile kinachoruhusiwa, kwa sababu kila kitu kinakataliwa kwa msingi.
Kuhesabu RBAC
# Get current privileges
kubectl auth can-i --list
# use `--as=system:serviceaccount:<namespace>:<sa_name>` to impersonate a service account
# List Cluster Roles
kubectl get clusterroles
kubectl describe clusterroles
# List Cluster Roles Bindings
kubectl get clusterrolebindings
kubectl describe clusterrolebindings
# List Roles
kubectl get roles
kubectl describe roles
# List Roles Bindings
kubectl get rolebindings
kubectl describe rolebindings
Kutumia Majukumu/ClusterRoles kwa Kuongeza Mamlaka
Abusing Roles/ClusterRoles in Kubernetes
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
 HackTricks Cloud
HackTricks Cloud