Kubernetes OPA Gatekeeper bypass
Tip
Learn & practice AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Learn & practice Az Hacking:HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
The original author of this page is Guillaume
Abusing misconfiguration
Enumerate rules
Having an overview may help to know which rules are active, on which mode and who can bypass it.
With the CLI
$ kubectl api-resources | grep gatekeeper
k8smandatoryannotations constraints.gatekeeper.sh/v1beta1 false K8sMandatoryAnnotations
k8smandatorylabels constraints.gatekeeper.sh/v1beta1 false K8sMandatoryLabel
constrainttemplates templates.gatekeeper.sh/v1 false ConstraintTemplate
ConstraintTemplate and Constraint can be used in Open Policy Agent (OPA) Gatekeeper to enforce rules on Kubernetes resources.
$ kubectl get constrainttemplates
$ kubectl get k8smandatorylabels
With the GUI
A Graphic User Interface may also be available to access the OPA rules with Gatekeeper Policy Manager. It is “a simple read-only web UI for viewing OPA Gatekeeper policies’ status in a Kubernetes Cluster.”
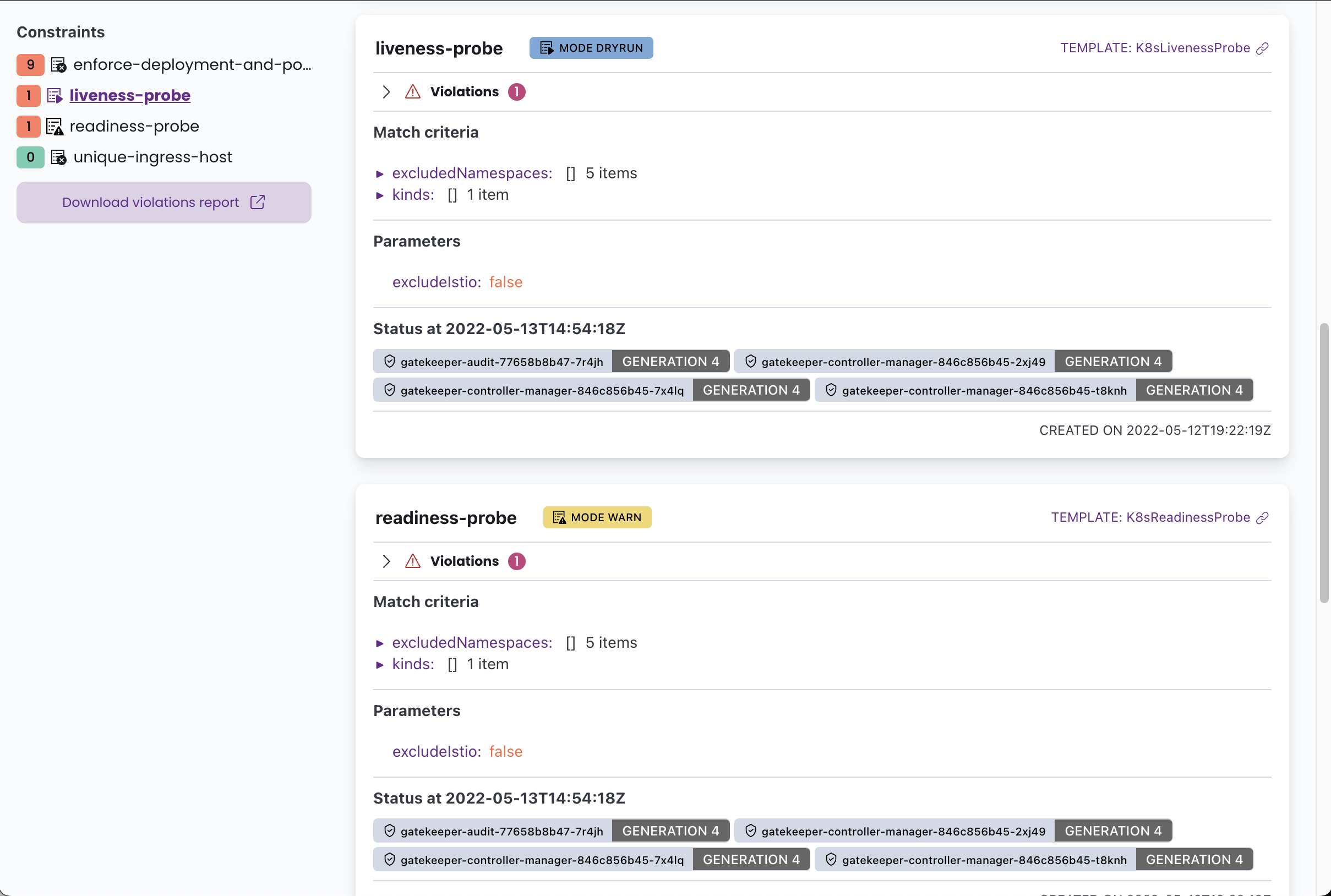
Search for the exposed service :
$ kubectl get services -A | grep gatekeeper
$ kubectl get services -A | grep 'gatekeeper-policy-manager-system'
Excluded namespaces
As illustrated in the image above, certain rules may not be applied universally across all namespaces or users. Instead, they operate on a whitelist basis. For instance, the liveness-probe constraint is excluded from applying to the five specified namespaces.
Bypass
With a comprehensive overview of the Gatekeeper configuration, it’s possible to identify potential misconfigurations that could be exploited to gain privileges. Look for whitelisted or excluded namespaces where the rule doesn’t apply, and then carry out your attack there.
Abusing Roles/ClusterRoles in Kubernetes
Abusing ValidatingWebhookConfiguration
Another way to bypass constraints is to focus on the ValidatingWebhookConfiguration resource :
Kubernetes ValidatingWebhookConfiguration
References
- https://github.com/open-policy-agent/gatekeeper
- https://github.com/sighupio/gatekeeper-policy-manager
Tip
Learn & practice AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Learn & practice Az Hacking:HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
 HackTricks Cloud
HackTricks Cloud